In our previous articles, We discussed firewall policy rules and FQDN Network Policies for implementing Fully Qualified Domain Name (FQDN) egress filtering in Google Cloud Platform(GCP). These options allow you to easily create rules to manage outbound traffic based on Fully Qualified Domain Names (FQDNs). However, they do not provide inspection and visibility capabilities for outbound traffic.
To address these limitations, the Secure Web Proxy (SWP) offers a solution by inspecting and enforcing policies on all outbound web traffic (HTTP/S) originating from your Google Cloud resources. SWP enhances the security of your egress traffic by providing comprehensive inspection and enforcement capabilities.
In this article, we will show you how to set up a Secure Web Proxy gateway in a Hub and Spoke network topology and guide you on verifying the setup in a client virtual machine (VM).
What is a Secure Web Proxy?
GCP Secure Web Proxy is a fully managed service that provides a secure and reliable way to access the Internet and SaaS applications from your Virtual Private Cloud (VPC) networks. It helps organizations enforce security policies, protect against web-based threats, and gain visibility into web traffic.
Advantages and Key Features of GCP Secure Web Proxy Compared to Other Proxy Services:
- Security: The service provides URL filtering, which allows you to enforce access control policies based on URL categories. It can inspect TLS traffic, which allows you to enforce security policies, such as inspecting for malware or enforcing content filtering. It also integrates with Google Cloud’s Threat Intelligence to protect against known malicious websites and phishing attacks.
- Granular access control: Secure Web Proxy (SWP) policies allows you to create rules that define how outbound web traffic flows from your Google Cloud resources to the internet. Policies can be used to restrict traffic based on the source of the traffic, destination, type of traffic, or a combination of these factors.
- Visibility and monitoring: Secure Web Proxy integrates with Cloud Logging and Cloud Monitoring, so you can easily collect and analyze logs and metrics for your egress web traffic.
- Scalability and reliability: GCP Secure Web Proxy is a fully managed service that automatically scales with your traffic, ensuring high availability and performance.
- Operational time savings: Secure Web Proxy doesn’t have VMs to set up and configure, doesn’t require software updates to maintain security, and offers elastic scaling. After initial policy configuration, a regional Secure Web Proxy instance works out of the box.
- Cost-effectiveness: The service is priced on a pay-as-you-go basis, so you only pay for the resources you use, and no upfront commitment is required.
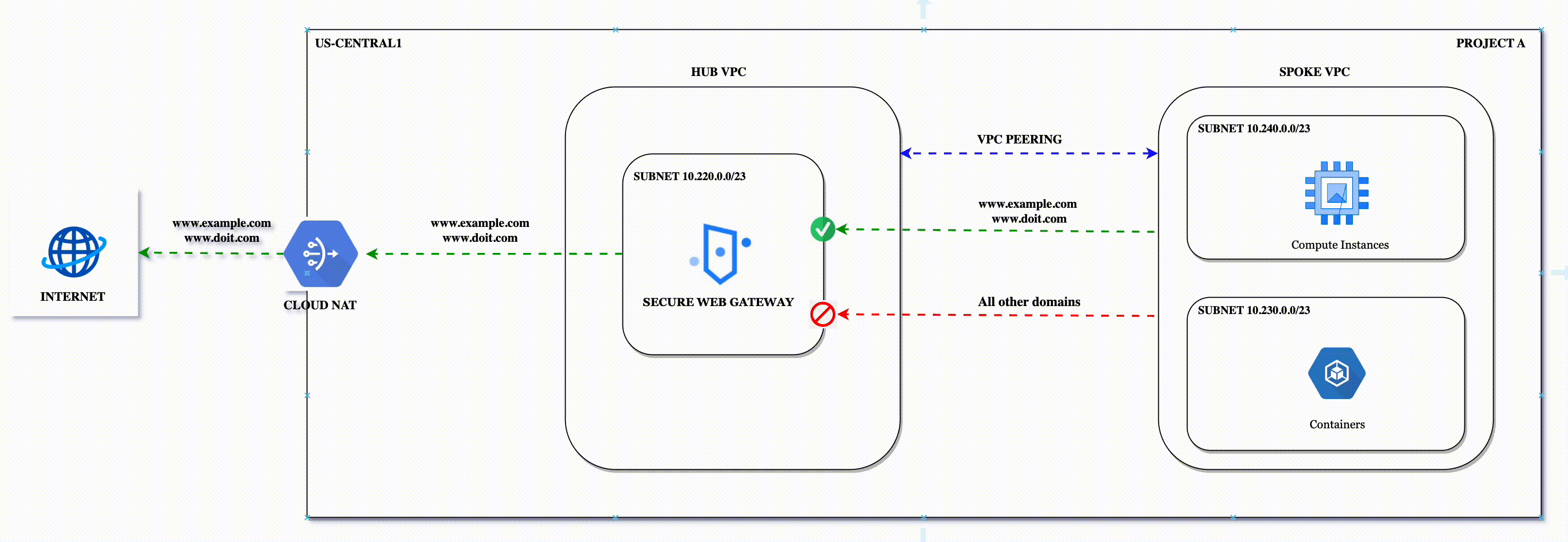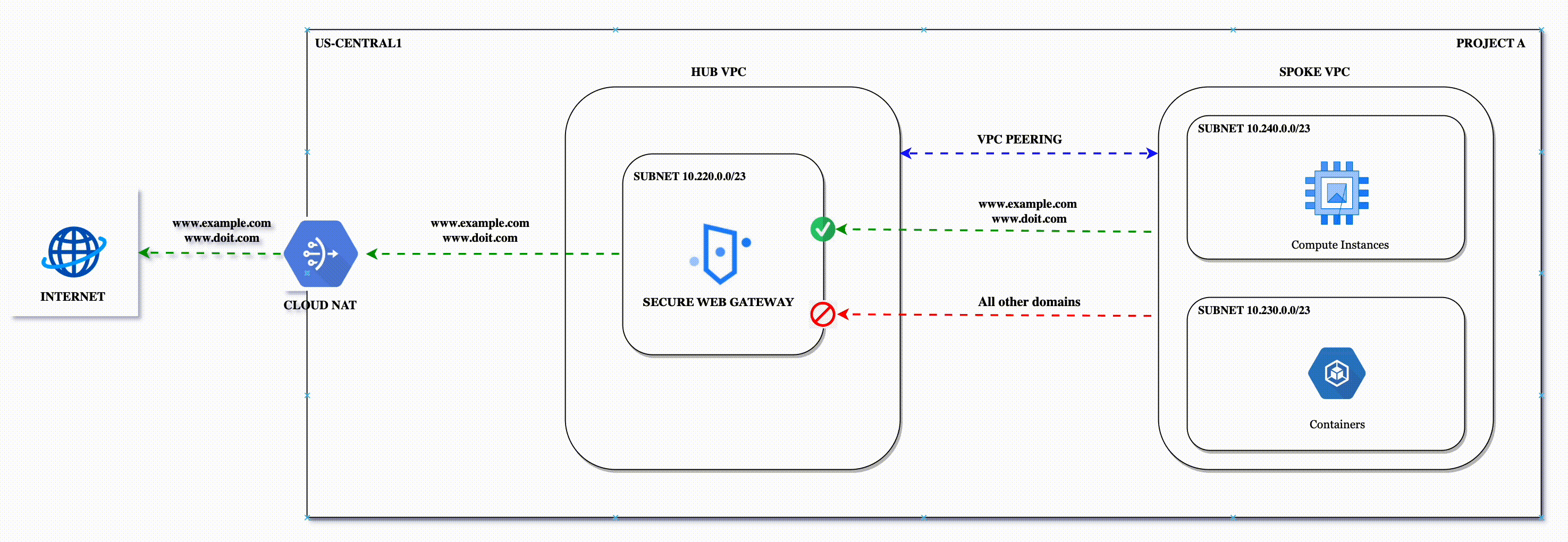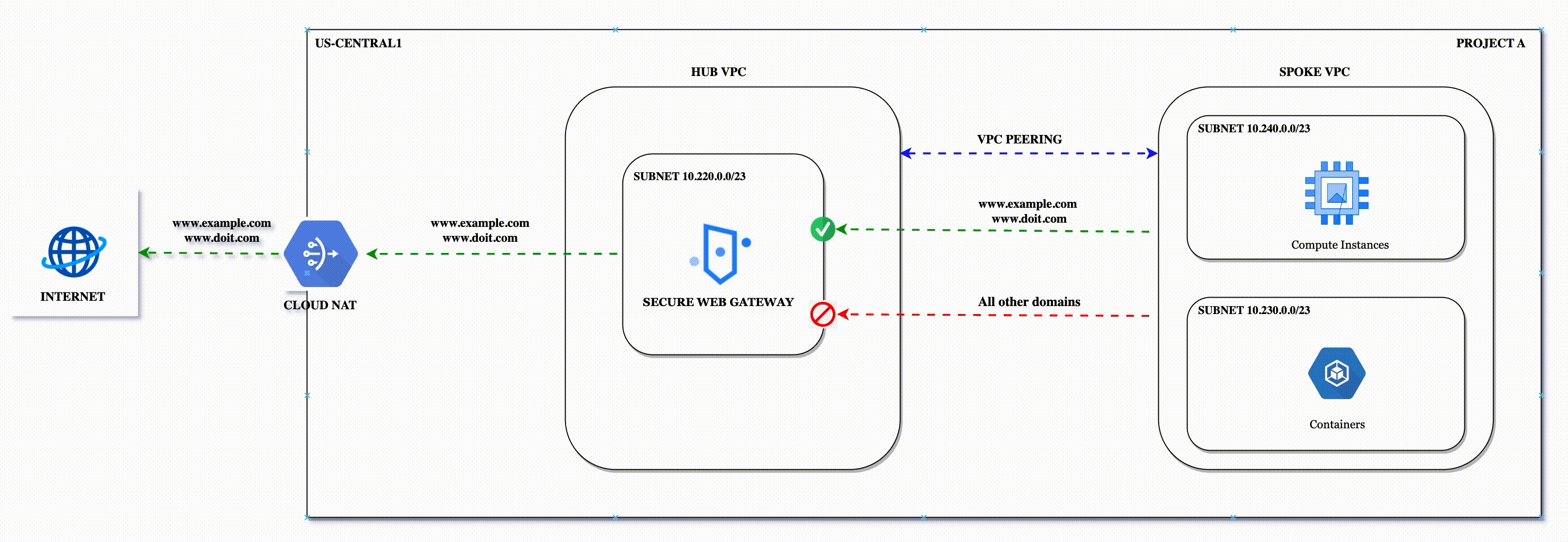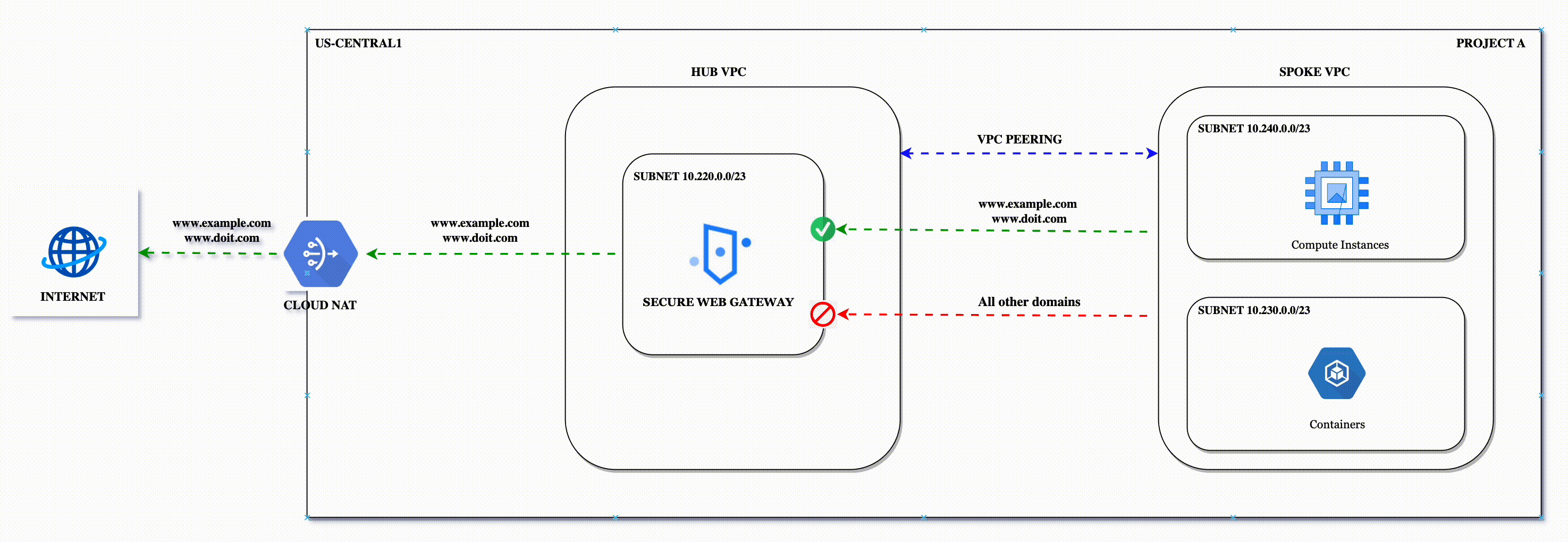
Reference Design
In this setup, the Secure web proxy instances are deployed in HUB VPC, and workloads are deployed in Spoke VPC. All the outbound requests will be forwarded to the Secure web proxy via VPC peering.
High-level architecture of the sample Hub and Spoke setup
Setup Secure Web Proxy and Validate Egress Web Traffic
Step 1: Setup up the necessary environment variables.
export PROJECT_ID="your-project-id" export REGION="your-region" export HUB_VPC="hub" export HUB_SUBNET="hub-subnet" export HUB_SWP_SUBNET="swp-subnet" #proxy only subnet export SPOKE_VPC="spoke" export SPOKE_GCE_SUBNET="spoke-gce-subnet" export SWP_CERT_NAME="swp-certificate" export SWP_POLICY_NAME="swp-policy"
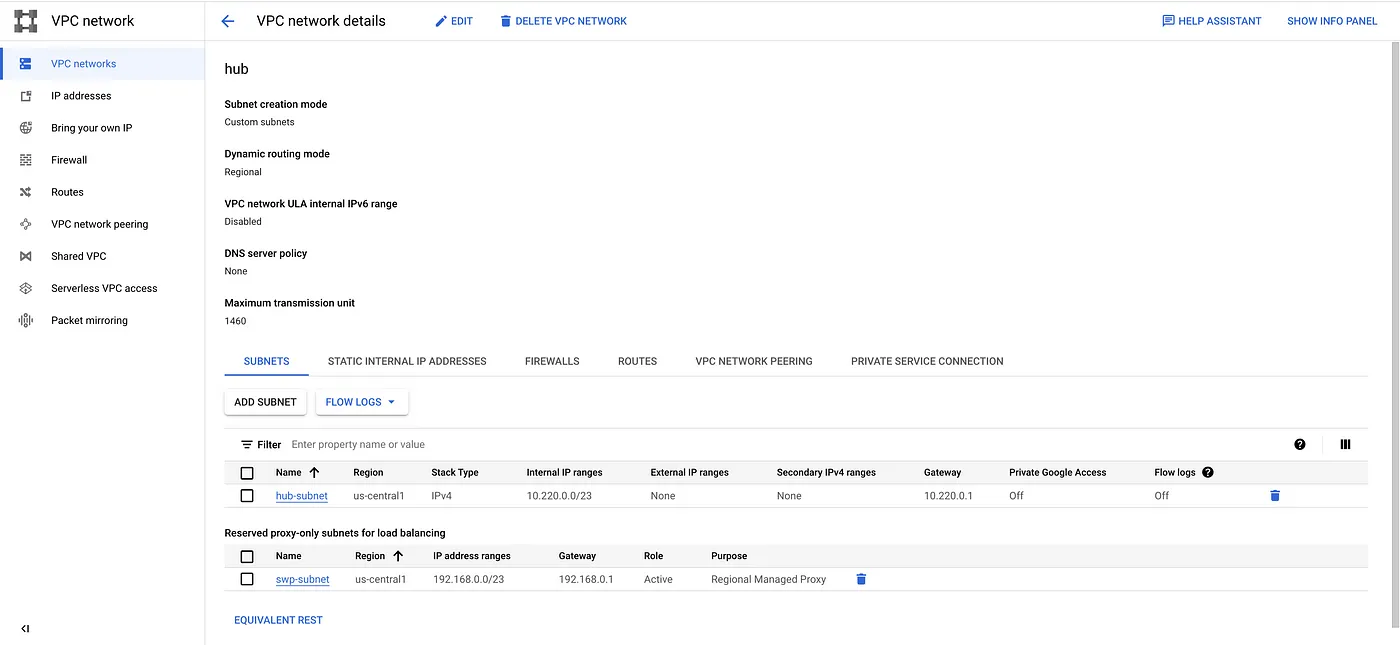
Step 2: Create the Hub network and subnet.
# Create a Hub custom Network gcloud compute networks create $HUB_VPC \ --project=$PROJECT_ID \ --subnet-mode=custom # Create the Hub nework subnet gcloud compute networks subnets create $HUB_SUBNET \ --project=$PROJECT_ID \ --network=$HUB_VPC \ --role="ACTIVE" \ --purpose="PRIVATE" \ --range=10.220.0.0/23 --region=$REGION
Step 3: Create a proxy subnet for Secure Web Proxy. The recommended subnet size is /23, or 512 proxy-only addresses because Secure Web Proxy connectivity is provided by a pool of IP addresses reserved for Secure Web Proxy.
This pool allocates unique IP addresses on the egress side of each proxy for interaction with Cloud NAT and destinations in the VPC network. Ensure the proxy range does not overlap with other networks.
# Create proxy only subnet for SWP. gcloud compute networks subnets create $HUB_SWP_SUBNET \ --project=$PROJECT_ID \ --network=$HUB_VPC \ --role="ACTIVE" \ --purpose="REGIONAL_MANAGED_PROXY" \ --range=192.168.0.0/23 --region=$REGION
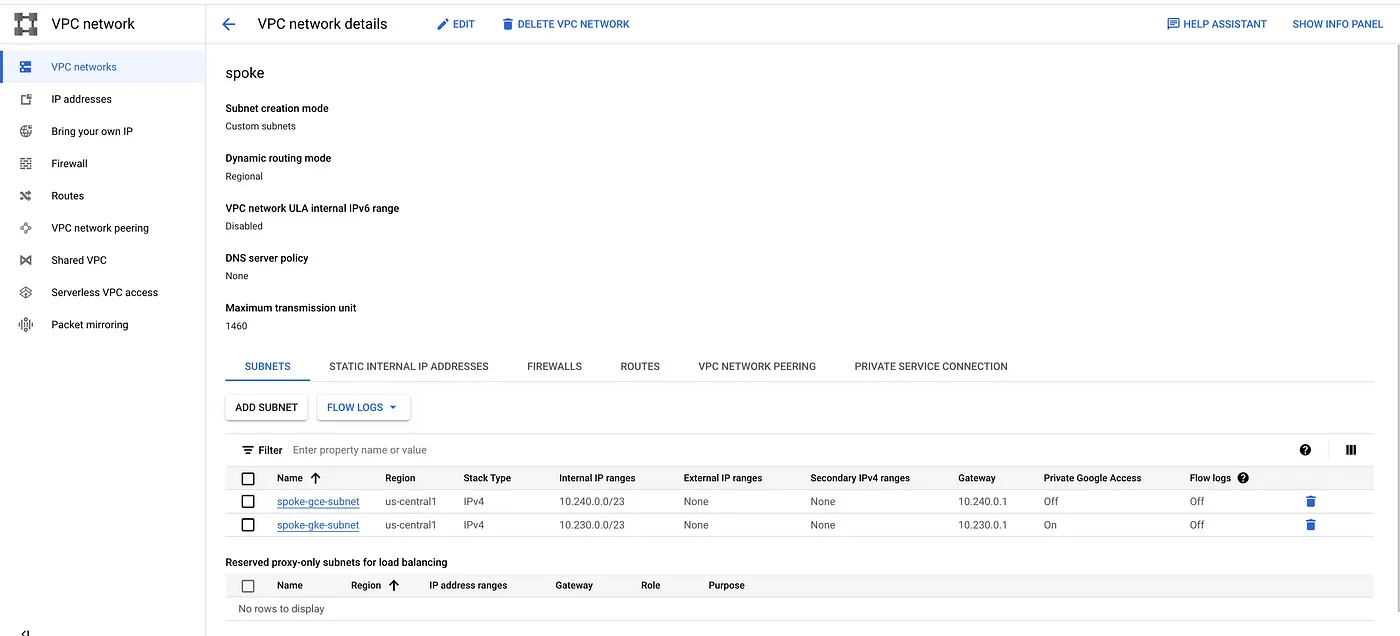
Step 4: Create the Spoke network and subnets.
# Create a Spoke custom Network and its subnet
gcloud compute networks create $SPOKE_VPC \
--project=$PROJECT_ID \
--subnet-mode=custom
gcloud compute networks subnets create $SPOKE_GCE_SUBNET \
--project=$PROJECT_ID \
--network=$SPOKE_VPC \
--range=10.240.0.0/23 --region=$REGION
Step 5: Delete the default internet route for Spoke VPC, and all the outbound traffic will be routed via the Hub VPC.
# Get the Default Route internet and the delete the rule ROUTE_NAME=$(gcloud compute routes list --filter="network: $SPOKE_VPC AND nextHopGateway:default-internet-gateway" --format="value(name)") gcloud compute routes delete $ROUTE_NAME --quiet
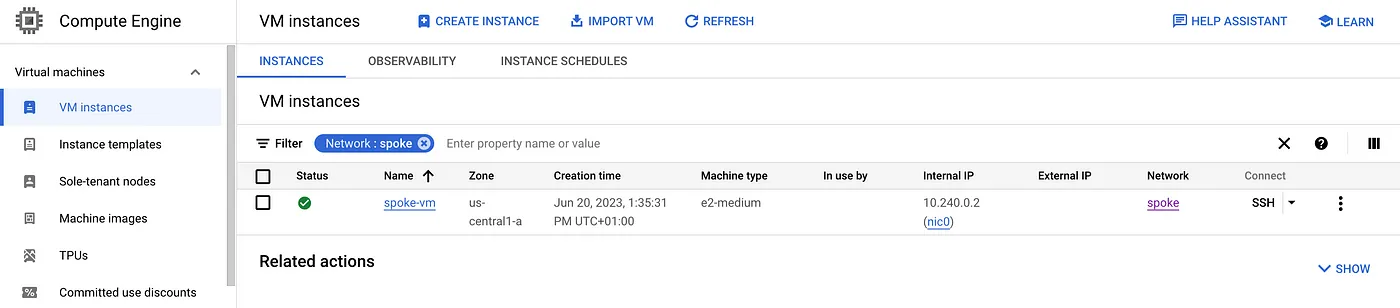
Step 6: Create a test Compute Engine instance in the Spoke Network.
# Create VM
gcloud compute instances create spoke-vm \
--zone=${REGION}-a \
--machine-type=e2-medium \
--network-interface=stack-type=IPV4_ONLY,subnet=${SPOKE_GCE_SUBNET},no-address \
--project=$PROJECT_ID
# Allow ssh via IAP
gcloud compute firewall-rules create allow-ssh-ingress \
--project=$PROJECT_ID \
--direction=INGRESS \
--priority=1000 \
--network=$SPOKE_VPC \
--action=ALLOW \
--rules=tcp:22 \
--source-ranges="35.235.240.0/20"
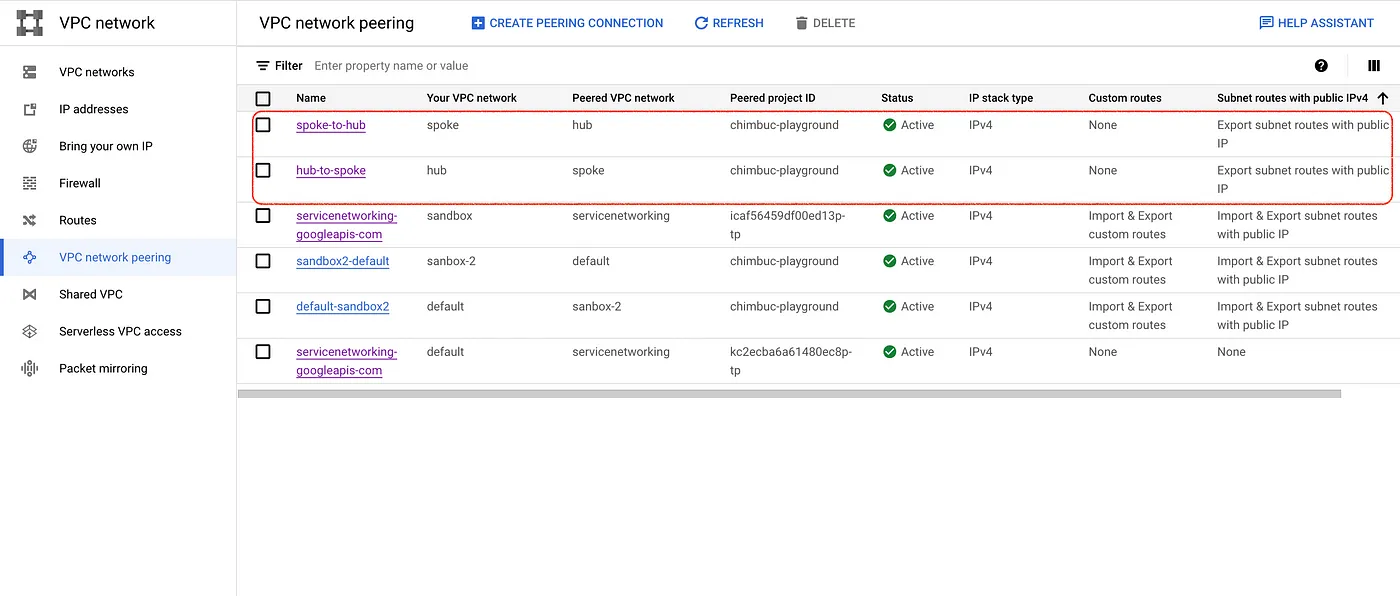
Step 7: Create VPC peering between Hub and Spoke VPC Networks.
# Hub to spoke gcloud compute networks peerings create hub-to-spoke \ --project=$PROJECT_ID \ --network=$HUB_VPC --peer-network=$SPOKE_VPC \ --auto-create-routes # Spoke to Hub gcloud compute networks peerings create spoke-to-hub \ --project=$PROJECT_ID \ --network=$SPOKE_VPC --peer-network=$HUB_VPC \ --auto-create-routes
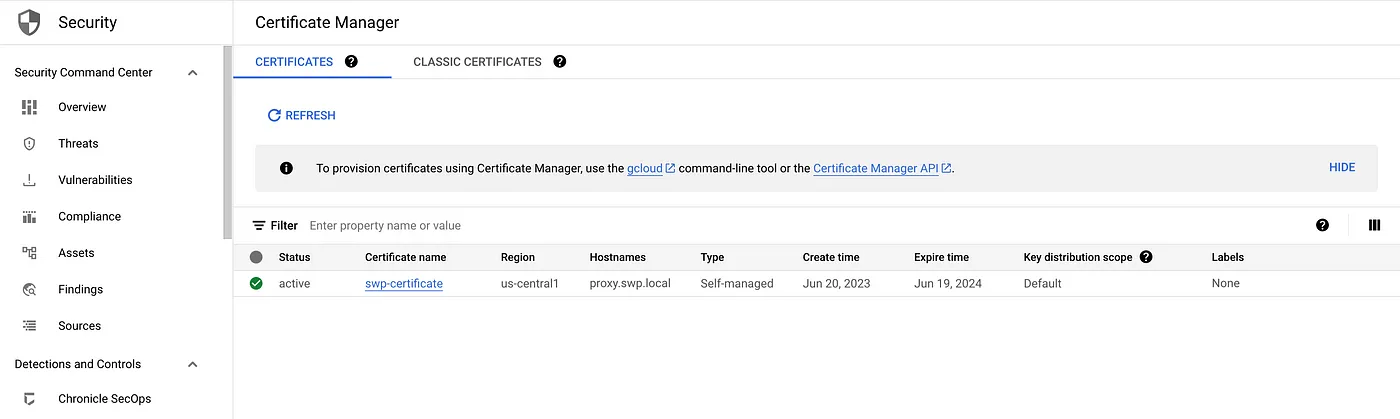
Step 8: The Secure Web Proxy Gateway will manage the TLS traffic, and we need to provide a certificate. This is the certificate that the client uses to authenticate with the proxy, Create an SSL certificate and upload the certificate to the certificate manager.
#create the certificate openssl req -x509 -newkey rsa:2048 \ -keyout key.pem \ -out cert.pem -days 365 \ -subj '/CN=demo.swp.local' -nodes -addext \ "subjectAltName=DNS:demo.swp.local" #upload the certificate gcloud certificate-manager certificates create $SWP_CERT_NAME \ --certificate-file=cert.pem \ --private-key-file=key.pem \ --location=$REGION
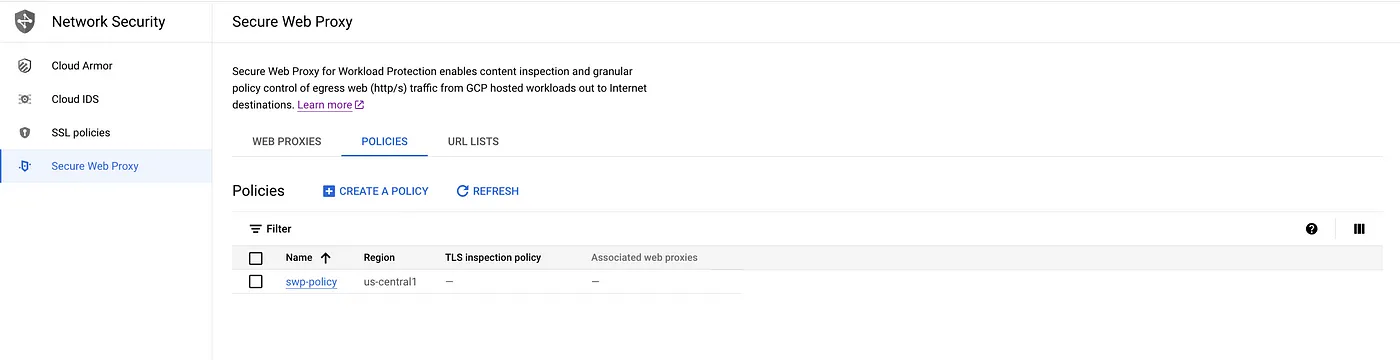
Step 9: Create a Secure Web Proxy policy.
Secure Web Proxy also offers a TLS inspection service that lets you intercept the TLS traffic, inspect the encrypted request, and enforce security policies. Refer to the TLS inspection overview for sample configurations.
#Sample policy without enable TLS inspection. cat << EOF > swp-policy.yaml description: Secure Web Proxy policy name: projects/$PROJECT_ID/locations/$REGION/gatewaySecurityPolicies/$SWP_POLICY_NAME EOF gcloud network-security gateway-security-policies import $SWP_POLICY_NAME \ --source=swp-policy.yaml \ --location=$REGION
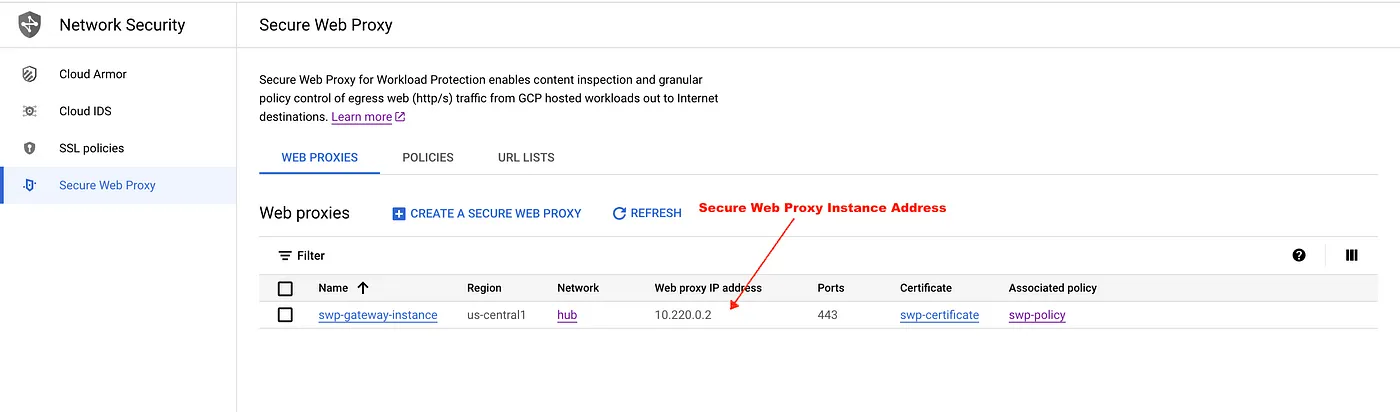
Step 10: Create a secure web proxy gateway instance with the policy created in the previous step.
# Create config file
cat << EOF > swp-gateway.yaml
name: projects/$PROJECT_ID/locations/REGION/gateways/swp-gateway
type: SECURE_WEB_GATEWAY
ports: [443]
certificateUrls: ["projects/$PROJECT_ID/locations/$REGION/certificates/$SWP_CERT_NAME"]
gatewaySecurityPolicy: projects/$PROJECT_ID/locations/$REGION/gatewaySecurityPolicies/$SWP_POLICY_NAME
network: projects/$PROJECT_ID/global/networks/$HUB_VPC
subnetwork: projects/$PROJECT_ID/regions/$REGION/subnetworks/$HUB_SUBNET
scope: basic-scope
EOF
gcloud network-services gateways import swp-gateway-instance \
--source=swp-gateway.yaml \
--location=$REGION
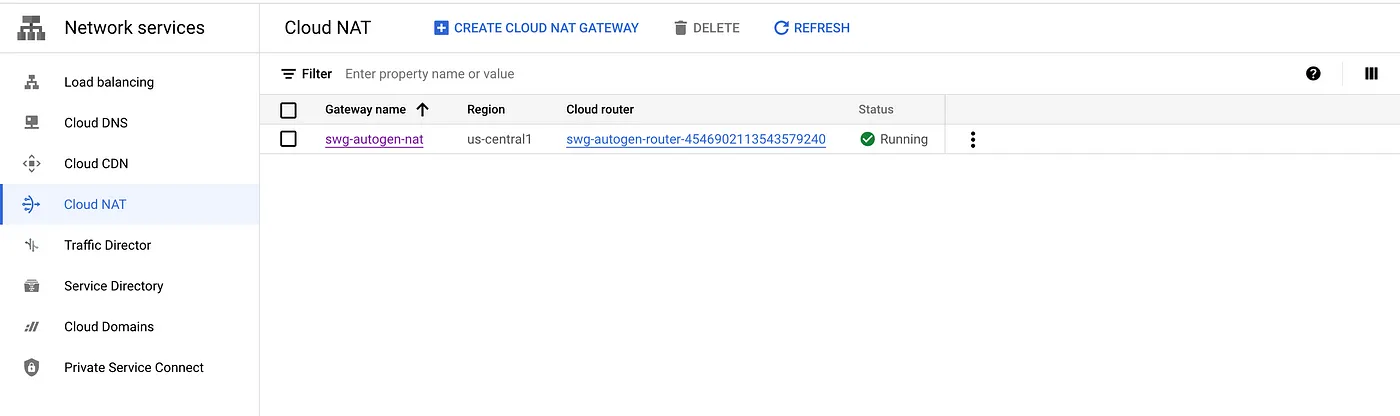
A Cloud NAT gateway is created to enable internet access when you provision a Secure Web Proxy instance. Only Secure Web Proxy endpoints in that region and network can access the Cloud NAT gateway. No other endpoint, such as a virtual machine (VM) instance or a Google Kubernetes Engine (GKE) node, is allowed to route traffic through the gateway.
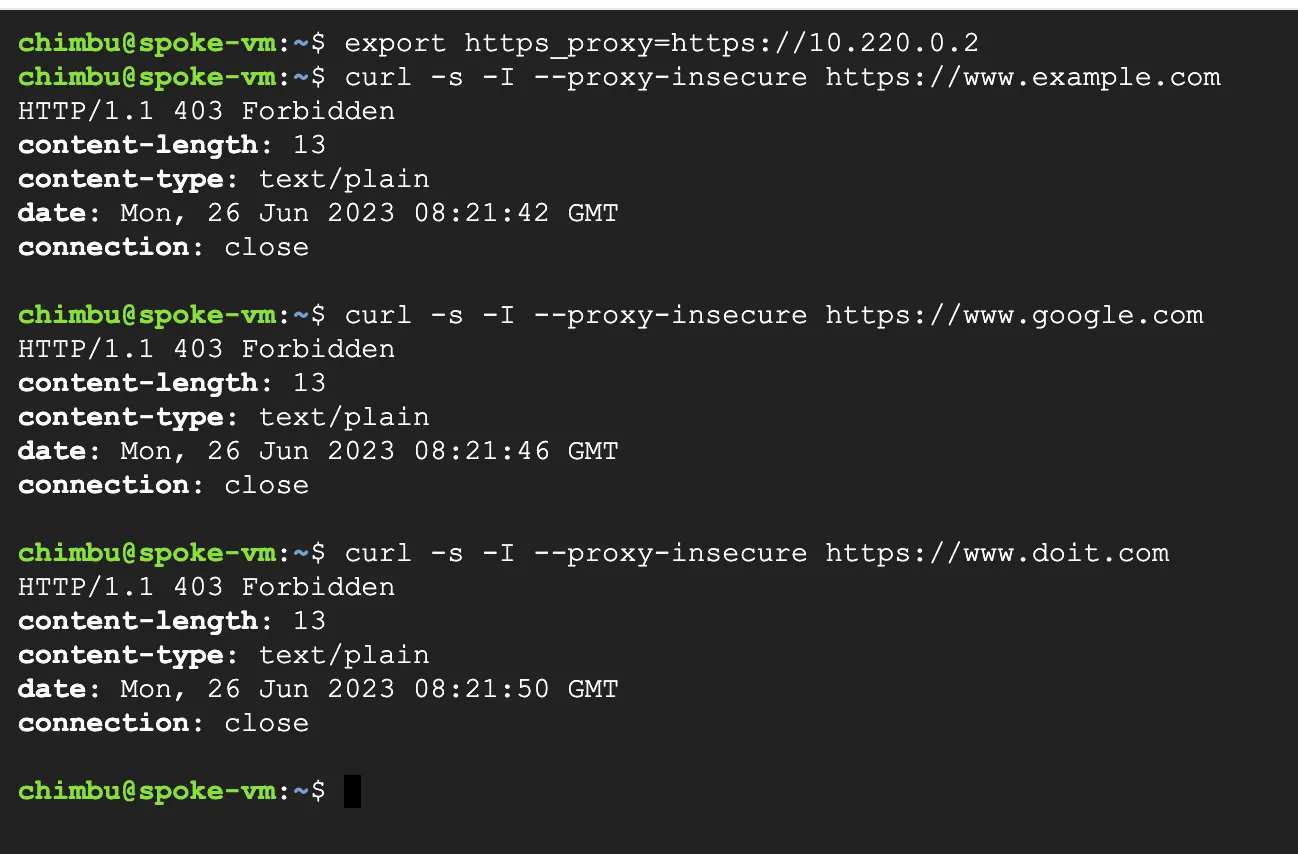
Step 11: SSH into the test instance in the Spoke network to validate the egress requests. The Secure Web Gateway Proxy policy is not configured with rules, so all the outbound traffic will be denied by default.
#sample commands #replace $SWP_HOST_IP with the IP address of the SWP Gateway IP $export https_proxy=https://$SWP_HOST_IP $curl -s -I --proxy-insecure https://www.example.com
Results from the Test Instance
Step 12: Create secure web proxy rules to allow and deny outbound traffic based on the reference architecture.
A Secure Web Proxy (SWP) rule is a statement that defines how outbound web traffic is handled by the proxy.
The example policy allows the outbound connection based on the hostname. Refer to the CEL matcher language for the full list of attributes and operators.
#allow www.example.com,The rule with the lowest numeric value assigned has the highest logical priority and is evaluated prior to rules with lower logical priorities.
cat << EOF > allow-example-com.yaml
name: projects/$PROJECT_ID/locations/$REGION/gatewaySecurityPolicies/$SWP_POLICY_NAME/rules/allow-example-com
description: Allow example.com
enabled: true
priority: 1000
basicProfile: ALLOW
sessionMatcher: host() == 'www.example.com'
EOF
gcloud network-security gateway-security-policies rules import allow-example-com \
--source=allow-example-com.yaml \
--location=$REGION \
--gateway-security-policy=$SWP_POLICY_NAME
#allow www.doit.com
cat << EOF > allow-doit-com.yaml
name: projects/$PROJECT_ID/locations/$REGION/gatewaySecurityPolicies/$SWP_POLICY_NAME/rules/allow-example-com
description: Allow example.com
enabled: true
priority: 999
basicProfile: ALLOW
sessionMatcher: host() == 'www.doit.com'
EOF
gcloud network-security gateway-security-policies rules import allow-doit-com \
--source=allow-doit-com.yaml \
--location=$REGION \
--gateway-security-policy=$SWP_POLICY_NAME
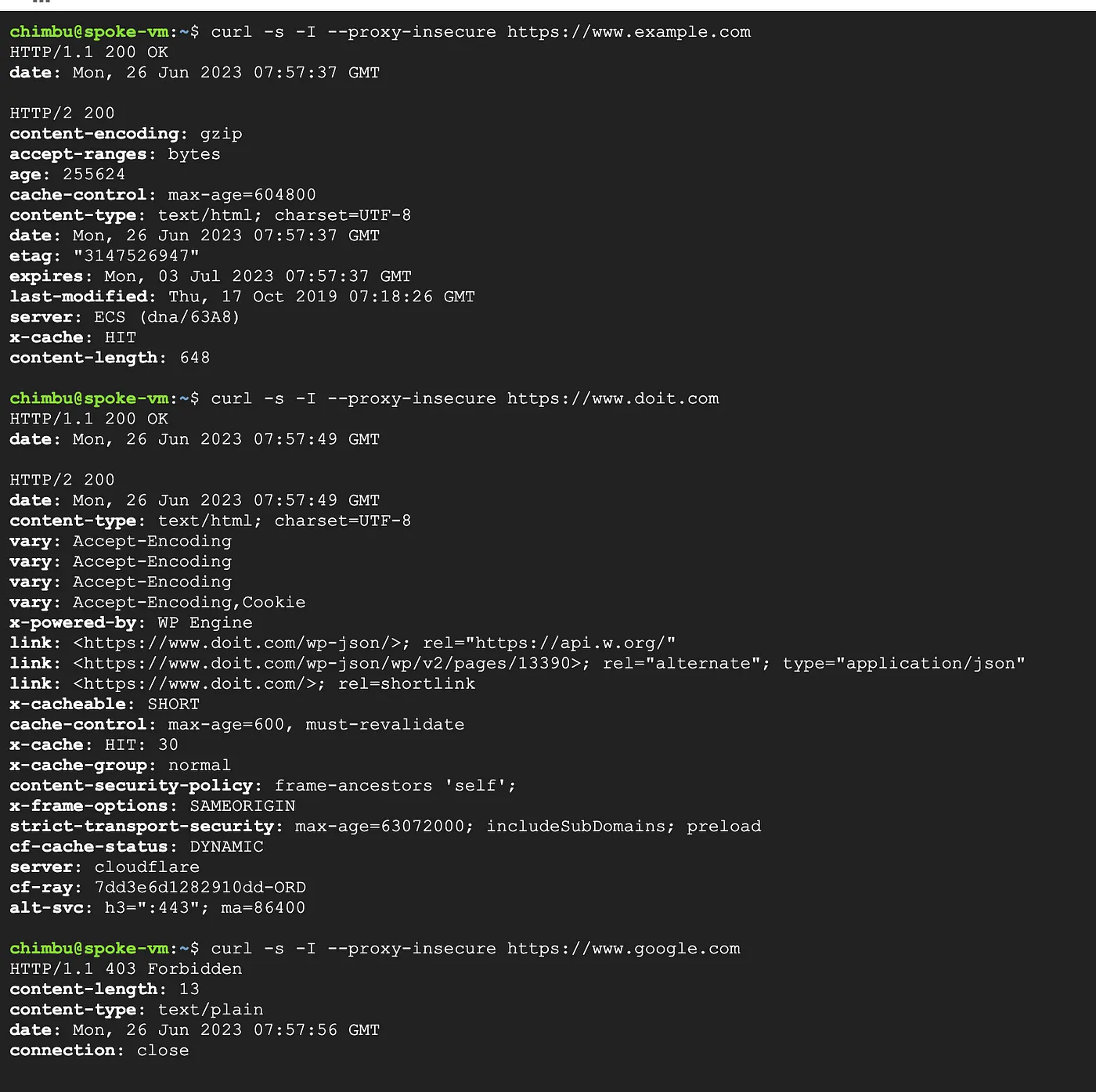
Results from the test Instance
From the above test results, we can observe that the Secure Web Proxy Gateway permits outbound connections exclusively to the allowed hostnames specified in the rules, while connections to other domains are prohibited.
Conclusion
Following the outlined steps, users can set up and validate the Secure Web Proxy (SWP) gateway in their network topology, enabling access to secure and controlled Internet and SaaS applications.
We hope this blog post has been helpful. For more information, please refer to the following resources: