As cloud environments grow more complex, organizations are increasingly turning to FinOps automation to manage costs and drive efficiency at scale. But deploying an automation solution isn't always an easy sell, particularly within larger enterprises where cloud finance, governance, and security responsibilities are often spread across multiple teams and departments, and accountability is a critical concern across the board.
Given DoiT’s experience working with over 4,000 customers around the world, these concerns were top of mind when building and deploying CloudFlow. This no-code workflow automation solution within DoiT Cloud Intelligence™ enables teams to speed up time to savings and maintain better cloud governance by putting repetitive optimization tasks on autopilot.
Let’s look at some of the most pressing questions that some of our enterprise clients face when adopting a new FinOps automation solution, and how CloudFlow helps answer them.
1. Security Risks: "Who’s touching our cloud?"
Given the importance of security and the scope of most enterprise security teams’ responsibilities, it’s no surprise that this is one of the most common objections that larger organizations have around automation tools. The concern typically stems from uncertainty around who will have excessive access to sensitive cloud data or the ability to make unauthorized changes in their cloud environment(s).
How CloudFlow addresses it:
- Identity & access restrictions: Only users with a DoiT Admin role are able to execute changes in production environments. By granting this role only to individuals who also have those permissions in your cloud environment, it ensures that no unauthorized user can affect the environment or end-user experience.
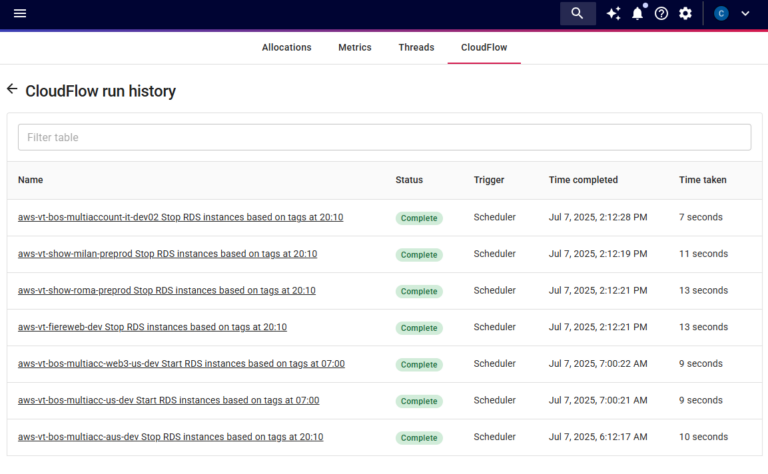
- Auditability: CloudFlow keeps a detailed history of every time a flow is executed, regardless of whether it was completed or encountered errors. All actions – including approvals and notifications – are logged and attributable to individual users within the DoiT console, giving InfoSec and compliance teams the accountability guardrails that they require.
2. Cloud Governance: "Will automation break our rules?"
Common Objection: Cloud governance policies are already a sore subject for many FinOps and DevSecOps practitioners. Adhering to established governance policies like tagging standards, naming conventions, and cost attribution rules is critical to maintaining cloud operations, and any automation tool that can bypass those standards is going to be met with skepticism.
How CloudFlow addresses it:
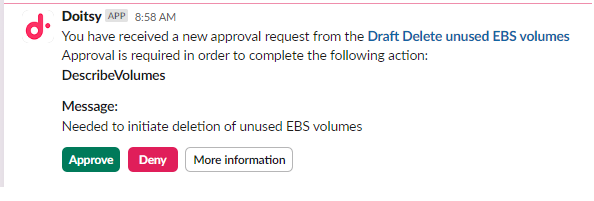
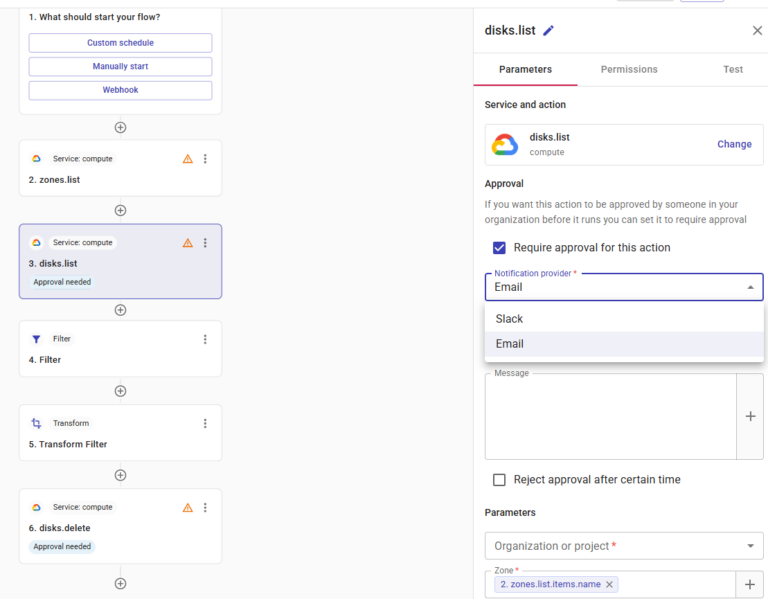
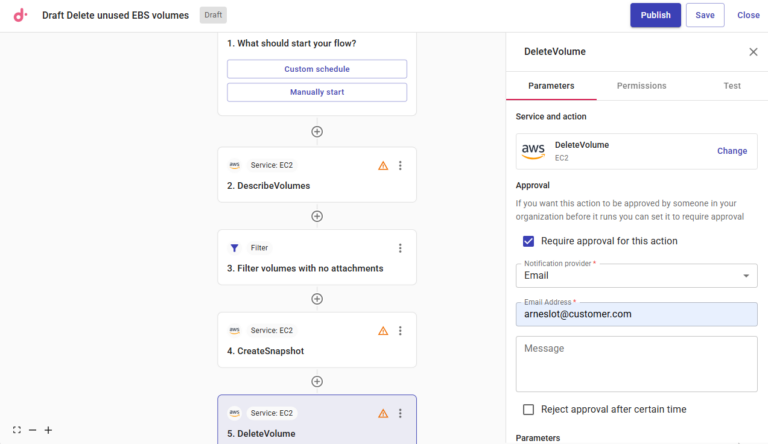
- Approval requirements: Every step of an automation flow can require approval from stakeholders (e.g., FinOps, engineering, or finance), enforcing accountability and ensuring that no changes are made to the environment without getting express authorization from the right people in the organization, giving governance teams time to review changes before they’re executed.
- Data-rich notifications: In addition to explicit approvals, users can add notification steps at any point in a flow to send timely updates and alerts within workflows outside of the approval flow. This enhanced data referencing allies you to pull in and utilize data from any part of a CloudFlow for more helpful and informative notifications.
- Enhanced governance operations: Rather than breaking governance standards, CloudFlow can actually be used to improve teams’ governance discipline by automating operations that might otherwise get overlooked or de-prioritized. For example, CloudFlows can be run on a regular basis to automatically clean up untagged or improperly tagged workloads, or autonomously shut down any idle instances that have been running for a given length of time.
3. Loss of Control: "We’re not ready for self-flying cloud operations."
Common Objection: Teams fear that automation will act as a “black box,” executing changes behind the scenes with little transparency. Without clear visibility into what actions were taken, by whom, and why, teams worry about losing control, especially if something goes wrong and there's no easy way to understand or undo the change.
How CloudFlow addresses it:
- Manual approvals, step-by-step notifications, & wait states: Stakeholders can receive alerts at any stage of the automation, with full context and outcomes. In addition to these alerts, manual approvals can be built into any step in the process so that they can only proceed after human review, blending automation with oversight.
- Visibility into change history: CloudFlow provides a complete audit trail of who approved, paused, or rejected any change, thus providing the accountability needed by governance and security teams, as well as a clear path to reversing any changes that might have been approved in error.
4. Integration Complexity: "It won’t work with our stack."
Common Objection: Enterprises often rely on a mature ecosystem of tools for CI/CD pipelines, cost monitoring, ticketing, and incident management. Introducing a new automation platform can be seen as redundant or disruptive, especially if it doesn’t integrate well with existing workflows. Teams may be reluctant to adopt another system that adds operational overhead or creates silos instead of enhancing the tools they already trust.
How CloudFlow addresses it:
- No agent required: CloudFlow’s no-code, API-driven automation avoids the performance overhead of agents or complex infrastructure changes. Users have the whole library of AWS and Google Cloud, and APIs available within the UI, giving you the ability to do anything that you could do in the cloud provider consoles.
- Modular design: CloudFlow was built to integrate seamlessly into existing workflows, whether it’s notifying via Slack, triggering Jira tickets, or pausing for approvals. Flows can also be triggered by custom webhooks, making it easy to correlate an event in one platform with a corresponding CloudFlow, such as shutting down an instance when a security alert is triggered.
5. Financial Concerns: "Is it worth the investment?"
Common Objection: Even tools built to reduce cloud spend face tough financial scrutiny – especially ones that operate as independent third-party solutions with high price tags that must then be integrated into existing tools. Budget owners want clear, immediate justification for any new expense, and if the ROI isn’t measurable or fast-acting, the tool may be seen as an unnecessary cost rather than a value driver.
How CloudFlow addresses it:
- Native DoiT solution: As a native feature within DoiT Cloud Intelligence, CloudFlow comes as part of the licensing subscription and requires no configuration to integrate with the rest of the platform. Users can take immediate action on FinOps recommendations surfaced by DoiT, and triggering flows with actions from external tools can be done with a simple Webhook.
- Faster time to savings: By reducing manual toil and speeding up action on cost anomalies, CloudFlow accelerates the FinOps resolution process, and in doing so lowers mean time to resolution and accelerates the time to savings.
FinOps automation doesn’t have to mean loss of control
Enterprise-grade FinOps automation must do more than identify opportunities – it must empower organizations to act on them safely, predictably, and in alignment with existing controls. With features like identity restrictions, approval checkpoints, and customizable notifications, CloudFlow makes it possible to scale cloud cost management without sacrificing operational efficiency, security, or visibility.